How-to Guides
How to Know If Someone Logged Into Your WhatsApp (Complete 2026 Guide)
how to know if someone logged into your WhatsApp. WhatsApp is one of the most widely used messaging apps in the world, and because it contains personal chats, photos, videos, and even private business conversations, security is extremely important. Many users worry about one question:
How to know if someone logged into your WhatsApp without your permission?
If you have noticed unusual activity on your WhatsApp account or feel your privacy may be compromised, this guide will help you identify the signs, check your account security, and protect your WhatsApp from hackers or unauthorized access.
This article explains everything step by step in simple language.
Can Someone Log Into Your WhatsApp?
Yes, it is possible.
Someone can access your WhatsApp in these common ways:
- By linking your WhatsApp to WhatsApp Web
- By getting access to your phone temporarily
- By using spy apps or malware
- By tricking you into sharing a verification code
WhatsApp does not allow two phones to use the same account independently, but linked devices can silently monitor your chats if you are not careful.
How to Know If Someone Blocked You on WhatsApp
1. Check Linked Devices (Most Important Step)
This is the most reliable way to know if someone logged into your WhatsApp.
How to Check on Android:
- Open WhatsApp
- Tap the three dots (⋮) in the top right
- Select Linked Devices
How to Check on iPhone:
- Open WhatsApp
- Go to Settings
- Tap Linked Devices
What to Look For:
- Unknown devices (Windows, Mac, browsers)
- Login locations you don’t recognize
- Active sessions when you never logged in
If you see a suspicious device, tap it and choose “Log out” immediately.
2. Messages Read Without You Opening Them
If your messages are being marked as read (blue ticks) even though you didn’t open them, this could be a red flag.
Possible reasons:
- Someone is reading your chats via WhatsApp Web
- A linked device is active in the background
Note: Sometimes read receipts sync late, so check other signs too.
3. Messages Sent That You Didn’t Send
One of the clearest warning signs is:
- Messages sent from your account that you don’t remember sending
- Replies sent while you were offline or asleep
This may indicate:
- Someone has temporary access to your phone
- Your WhatsApp Web is open on another device
4. Unexpected Logouts or Verification Messages
If WhatsApp suddenly logs you out and asks for verification, be alert.
Signs include:
- Receiving a WhatsApp verification code SMS you didn’t request
- Getting a message saying your number is being registered on another device
This usually means someone is trying to take over your account.
Never share your WhatsApp verification code with anyone not even friends.
5. New Contacts or Chats You Don’t Recognize
Check your chat list and contacts for:
- Unknown conversations
- Archived chats you never archived
- Deleted messages you didn’t delete
This could happen if someone accessed your account and tried to hide activity.
How to Protect Your Data Privacy Online
6. Phone Battery Draining Faster Than Usual
If your phone battery suddenly drains quickly, it may be due to:
- Spy apps running in the background
- Unauthorized WhatsApp syncing
Check:
- Battery usage stats
- Apps consuming unusual power
This sign alone is not proof, but combined with others, it becomes suspicious.
7. Phone Heating or Data Usage Spikes
Unusual phone behavior can indicate spying:
- Phone heats up when idle
- High mobile data usage even when not active
WhatsApp Web syncing chats can cause increased background activity.
8. Check WhatsApp Security Notifications
WhatsApp sends alerts when:
- Your security code changes
- A chat’s encryption key changes
Open a chat → Tap contact name → Look for encryption or security notifications.
While not always dangerous, unexpected changes can be suspicious.
9. Someone Knows Private Information You Never Shared
If someone mentions:
- Private chats
- Personal details
- Conversations only available on WhatsApp
This may indicate your account is being monitored.
What to Do If Someone Logged Into Your WhatsApp
If you suspect unauthorized access, act immediately.
1. Log Out of All Devices
- Go to Linked Devices
- Tap Log out from all devices
2. Enable Two-Step Verification
- Go to Settings → Account → Two-Step Verification
- Set a secure PIN
- Add an email for recovery
This prevents hackers even if they get your SIM.
3. Secure Your Phone
- Lock your phone with PIN, fingerprint, or Face ID
- Do not leave your phone unlocked
- Avoid installing unknown apps
4. Scan for Malware
- Remove suspicious apps
- Avoid unofficial WhatsApp mods (GB WhatsApp, FM WhatsApp)
These mods are highly unsafe.
5. Reinstall WhatsApp (If Needed)
As a last option:
- Back up your chats
- Uninstall WhatsApp
- Reinstall and verify again
This removes unauthorized sessions.
How to Prevent WhatsApp Hacking in the Future
Follow these safety tips:
Never share verification codes
Enable two-step verification
Regularly check linked devices
Avoid public computers for WhatsApp Web
Use official WhatsApp only
Keep your phone OS updated
How to Block Spam Calls on iPhone
Frequently Asked Questions (FAQ)
Can someone read my WhatsApp messages remotely?
Yes, through WhatsApp Web or linked devices if they have access once.
Does WhatsApp notify me when someone logs in?
Yes, you can see it in Linked Devices, but no pop-up alert is sent.
Can WhatsApp be hacked without my phone?
Usually no, unless you share the verification code or install spyware.
Is WhatsApp Web safe?
Yes, if you control the login and log out after use.
Final Thoughts
Your WhatsApp account holds sensitive personal data, and protecting it is essential. By regularly checking linked devices, enabling two-step verification, and staying alert to unusual activity, you can quickly detect if someone has logged into your WhatsApp.
If something feels wrong, trust your instincts and secure your account immediately.
How-to Guides
How to Remove a Virus from Android (Complete Guide 2026)

Your Android phone stores your photos, passwords, banking apps, and private messages. So when something feels wrong, panic is natural. Learning how to remove a virus from Android can save your data, money, and peace of mind. Most people say “virus,” yet the real threat is malware like spyware, adware, or ransomware. Still, the solution begins the same way. You need clear steps, smart tools, and calm action. In this guide, you will discover exactly how to remove a virus from Android safely. More importantly, you will learn how to protect your device so it stays secure long after the cleanup is done.
How to clean your phone from virus
First, pause and breathe. Panic causes mistakes. Smart action removes threats.
If you want to clean phone of malware, start with the basics. Clear unnecessary storage. Delete unknown apps. Check permissions. Many infections hide inside harmless-looking tools downloaded outside the Google Play Store.
Here is your first defense layer:
- Use clear cache Android from app settings
- Uninstall suspicious apps immediately
- Run a scan phone for malware using a trusted Android antivirus app
- Enable Google Play Protect
- Review mobile data usage for strange spikes
Sometimes the infection is simple Adware throwing Pop-up ads everywhere. Other times it is Battery draining malware secretly mining crypto. Think of malware like termites. You may not see them. Yet the damage grows quietly.
For example, a small flashlight app once requested microphone access. That is absurd. A flashlight needs light permission only. Such red flags scream trouble.
Here is a quick risk table:
| Symptom | Possible Cause | Immediate Action |
|---|---|---|
| Random ads | Adware | Remove unknown apps |
| Slow phone | Spyware or Rootkit | Run Malware scan |
| Locked screen | Ransomware | Disconnect internet |
| High data usage | Spyware | Check app permissions |
Small steps matter. They build real Android virus protection.
How to get rid of a virus on your Android phone: Step-by-Step
Now we go deeper. If your phone acts strange, follow this structured plan.
Start with isolation. Disconnect from WiFi. A Spoofed network or Public WiFi risk often spreads malware. Hackers love coffee shops.
Then restart in Safe Mode. This disables third-party apps. If the issue stops, a malicious app is the culprit. That narrows your hunt.
Next actions:
- Reboot in safe mode
- Remove malicious apps
- Change Google password
- Strengthen Google Account security
- Enable 2-Step Verification Android
- Activate Multi-Factor Authentication (MFA)
Why change passwords? Because many Trojan horse attacks steal credentials during a Phishing attack. A simple password reset can block a future Data breach.
For extra safety, install Malwarebytes or Malwarebytes Mobile Security from the official Google Play Store. A proper Malware scan detects hidden Keylogger or Rootkit threats invisible to you.
Here is a structured flow diagram:
Detect Issue
↓
Disconnect Internet
↓
Enter Safe Mode
↓
Delete suspicious apps
↓
Run antivirus for Android
↓
Update passwords
↓
Enable Android virus protection
Each step strengthens your mobile cybersecurity posture. Skip none.
Does resetting a phone remove a virus?
Factory reset sounds dramatic. Sometimes it is necessary.
Yes, factory reset Android can remove most malware. It wipes everything. Apps, files, hidden infections. However, it is a nuclear option.
Before resetting:
- Backup clean files only
- Avoid restoring infected apps
- Update the Android operating system after reset
Think of reset like demolishing a termite-infested house. You remove the structure. Yet if you reuse contaminated wood, termites return.
Important note. Advanced Rootkit infections rarely survive reset. Still, firmware-level attacks need professional repair.
According to Google Security Blog (https://security.googleblog.com), keeping system updates active reduces 95 percent of exploit-based attacks. Updates patch vulnerabilities quietly.
Reset wisely. Not blindly.
How to remove viruses from a phone that won’t turn on
A phone that refuses to boot feels terrifying. Yet do not assume the worst.
Often the issue is hardware. Sometimes severe Ransomware corrupts startup files. If recovery mode works, try factory reset from recovery.
If recovery fails, professional service is required. You cannot manually remove a Rootkit without specialized tools.
Here is your action ladder:
- Charge fully
- Attempt recovery mode reset
- Avoid random repair apps
- Contact manufacturer support
Do not download shady PC tools promising miracle Android malware removal. Many are scams.
When your device is dead, patience beats panic.
How do I know if my phone has a virus: How to check for viruses on Android
Your phone whispers before it screams. You must listen.
Warning signs include:
- Strange Pop-up ads
- Unknown Suspicious apps
- Rapid mobile data usage
- Fast battery drain
- Apps crashing
Here is a quick symptom checklist:
| Behavior | Risk Type |
|---|---|
| Contacts get spam texts | Trojan horse |
| Camera activates randomly | Spyware |
| Phone overheats idle | Keylogger or miner |
| Fake security alerts | Stalkerware |
Run a scan phone for malware using a reputable Android antivirus app. That gives clarity fast.
Malware vs Virus Difference Explained Simply
A virus spreads by attaching itself to files. Malware is broader. It includes Adware, Spyware, Ransomware, and more. So when you search how to remove a virus from Android, you actually mean removing malware. The solution focuses on secure Android phone practices and layered protection.
Understanding this difference improves decision-making.
Android virus protection
Protection beats repair. Always.
To strengthen Android virus protection, follow these rules:
- Use trusted antivirus for Android
- Keep system updated
- Enable Google Play Protect
- Avoid third-party app stores
- Use VPN for Android for encrypted browsing
- Follow Strong password tips
A VPN for Android adds Privacy protection especially on public WiFi. It encrypts traffic. Hackers see gibberish.

Good password structure:
- 12+ characters
- Mix of symbols and numbers
- No birthdates
Strong Password security blocks 80 percent of breaches instantly.
Security is not paranoia. It is discipline.
Cybersecurity info you can’t live without
Cybercrime evolves daily. Attackers innovate. You must adapt.
According to FBI IC3 reports (https://www.ic3.gov), Americans lose billions yearly to digital fraud. Many cases start with mobile compromise.
Essential knowledge:
- Never click random SMS links
- Verify app developer reputation
- Review permissions monthly
- Monitor banking alerts
Think of cybersecurity like locking your house. You would not leave doors open. So do not leave digital doors open.
Layered defense works best. Antivirus. MFA. VPN. Updates. Awareness. Combined, they create a fortress.
Privacy Preference Center
Privacy matters. Data is currency.
Control app permissions regularly. Visit settings and disable camera or microphone for apps that do not need them. That limits Spyware risks.
Also adjust Google ad personalization settings. Reduce tracking. Review Google Account security dashboard often.
Here is a simple privacy control table:
| Setting | Why It Matters |
|---|---|
| App Permissions | Prevent hidden spying |
| MFA Enabled | Stops stolen login abuse |
| Play Protect On | Blocks harmful apps |
| VPN Active | Shields browsing data |
Digital hygiene is like brushing teeth. Skip it and decay begins quietly.
Final Thoughts on How to Remove a Virus from Android
Learning how to remove a virus from Android empowers you. You are no longer helpless. You know how to remove virus from Android, perform Android malware removal, and build lasting Android device security.
Threats like Adware, Trojan horse, Spyware, and Ransomware will not disappear. However, with structured defense, awareness, and proactive tools, your phone stays secure.
Your Android holds your life. Protect it like it matters. Because it does.
FAQ
How do I manually remove a virus?
Go to Settings > Apps, find unfamiliar or suspicious apps, and uninstall them immediately.
Clear cache, review app permissions, and update your Android system to close security gaps.
How do I get rid of fake virus warning on Android phone?
Close the browser tab showing the alert and clear your browser cache and site data.
Do not tap the warning message, and avoid installing apps from pop-up ads.
How do I clean up and speed up my Android phone?
Delete unused apps, clear cache files, and remove large or duplicate media files.
Keep your software updated and disable background apps draining battery and memory.
What does *#0*# do on Android?
This code opens a hidden diagnostic test menu on some Samsung devices.
It allows you to test screen, sensors, speaker, and other hardware functions.
What does *#21 do to your Android phone?
This code checks call forwarding status on many mobile networks.
It does not hack your phone; it simply shows whether calls are being forwarded.
Related Artical
How-to Guides
How to Detect and Remove Spyware From an Android Phone 2026

Your Android phone carries your private world in its pocket. Messages, banking apps, passwords, and photos all live there. That is why learning how to Detect and Remove Spyware From an Android Phone is more important than ever. Spyware on Android often hides silently, acting as dangerous Malicious software that steals data without warning. This growing form of Mobile malware can expose your accounts to Cybercriminals and create serious Identity theft risks. You may not notice it at first. The signs can feel small and harmless. However acting quickly protects your privacy, money, and personal information from long-term digital damage.
What is spyware?
Spyware on Android is a form of Malicious software designed to secretly monitor your activity. It falls under the wider category of Mobile malware. Once installed, it collects sensitive data without your consent. This data may include passwords, browsing history, contacts, and even microphone recordings.
Some spyware acts like Hidden spy apps. Others operate as Phone monitoring apps or Stalkerware. Advanced threats such as a Remote access trojan (RAT) allow attackers to control your phone from anywhere. These programs often include Keyloggers, Password stealers, Banking trojans, and Information stealers. Even simple Cookie trackers can expose login sessions. In short, spyware turns your phone into a surveillance device.
What makes spyware so dangerous?
Spyware is dangerous because it attacks silently. You may notice Excessive battery drain or Phone overheating and assume your device is old. However, those symptoms can signal an Android security threat working in the background.
The real danger lies in stolen data. Login credentials theft leads to email compromise. Financial information theft can empty bank accounts. Worse, it may result in Identity theft, which takes months to repair. Many Cybercriminals use spyware to bypass Fraud prevention systems. Once inside your phone, they can read verification codes, intercept messages, and access banking apps. If you ever asked, “Why is my battery draining fast?” spyware might be the hidden answer.
Where does spyware come from?
Most infections begin with unsafe downloads. Users install apps outside the protection of Google Play Store vetting. These apps may look harmless but hide Malicious apps inside. Hackers also use Phishing scams through emails or text messages. One fake delivery link is enough to trigger infection.
Another common method involves permission abuse. Spyware often requests Device administrator permissions. Once granted, removal becomes difficult. Public Wi-Fi networks can also spread threats. When users download files on unsecured networks, attackers exploit vulnerabilities. To Avoid malicious app downloads, always verify the developer and read reviews carefully.
Spyware examples
Real-world spyware shows how serious this threat is. Pegasus is a high-profile surveillance tool that targeted journalists and officials. SpyNote steals messages and call logs. HiddenMiner secretly mines cryptocurrency and slows devices dramatically.
Below is a simplified comparison of known spyware families:
| Spyware Name | Main Function | Risk Level |
|---|---|---|
| Pegasus | Full surveillance | Critical |
| SpyNote | SMS and call tracking | High |
| Agent Smith | App replacement attack | High |
| HiddenMiner | Crypto mining | Medium |
Many Stalkerware apps pretend to offer parental control. In reality, they enable secret monitoring. If you want to Stop phone surveillance, understanding these examples helps you recognize patterns early.
How to detect spyware on Android phone
Learning How to detect spyware on Android phone begins with recognizing behavior changes. Spyware consumes resources. That leads to High data usage, slower performance, and overheating. If you search online for “Why is my phone running slow,” spyware may be the cause.

You should also inspect app permissions. Check for Suspicious app permissions like microphone access for a flashlight app. Monitor sudden spikes in data. Run a trusted Malware scan using reputable Antivirus software. To Detect unauthorized device access, review your Google account login history. Unfamiliar logins may signal compromise. These steps help you Monitor suspicious phone activity before serious damage occurs.
How to remove spyware from Android
Once you confirm infection, act quickly. Start by restarting your phone in Safe mode Android. Safe mode disables third-party apps temporarily. If issues stop, an app is responsible. Next, remove suspicious applications and revoke administrator rights.
After uninstalling unknown apps, perform Browser cache clearing to remove tracking scripts. Run a full Malware scan again. If spyware persists, perform a Factory data reset. This wipes all data and removes deep infections. Afterward, carefully Restore Android after factory reset using secure backups only. These steps explain clearly How to remove spyware from Android without professional tools.

Protect your Android phone from spyware
Prevention is stronger than repair. Regular Android OS updates patch security flaws. Enable Two-factor authentication (2FA) for all major accounts. Always use Secure websites (HTTPS) when entering passwords. These habits help you Protect personal data on mobile devices.
To Secure your smartphone from hackers, install reliable Antivirus software and keep Google Play Protect enabled. Avoid public USB charging ports. Never click unknown SMS links. These simple actions strengthen Mobile cybersecurity protection. They also help you Protect privacy on Android devices and prevent future infections.
How to Detect and Remove Spyware From an Android Phone
Let us bring everything together. First, identify warning signs such as overheating or unusual data spikes. Next, check permissions and run a security scan. Then remove suspicious apps using safe mode. Finally, reset the device if needed.
Understanding How to Detect and Remove Spyware From an Android Phone empowers you. It allows you to act before criminals exploit your information. Quick response reduces financial loss and prevents long-term damage.
Want to stay up to date on Kaspersky news?
Cyber threats evolve daily. Security researchers publish new findings each month. Following trusted cybersecurity sources keeps you informed about emerging Android security threat trends.
Staying updated helps you Protect your Android from stalker ware, detect new spyware strains, and adapt quickly. Cybersecurity is not a one-time task. It is an ongoing commitment.
for other guide please check this step by step guide How to Know If You Can Get Back a Deleted Facebook Account (7 Clear Steps)
Conclusion
Your Android phone is more than a device. It is your wallet, diary, and communication hub. Ignoring security risks invites trouble. Spyware thrives on silence and delay. Acting early makes all the difference.
Now you understand How to Detect and Remove Spyware From an Android Phone clearly and confidently. You know the warning signs. You know the removal steps. Most importantly, you know how to prevent future infections. Practice safe browsing. Update regularly. Question unusual behavior. When you take control of your digital habits, you shut the door on spyware for good.
Frequently Asked Questions (FAQ)
How do I check if there is spyware on my Android phone?
Look for unusual battery drain, high data usage, unknown apps, or strange pop-ups. Run a trusted antivirus scan and review app permissions in Settings.
How do I find hidden spy apps on my phone Android?
Check the full Apps list including system apps and review device administrator access. Remove unfamiliar apps and scan your phone with security software.
How do I know if my phone is being monitored on Android?
Signs include background call noises, overheating, messages marked as read, or sudden slow performance. Check account activity and change passwords immediately if suspicious.
How to remove spyware from Android phone for free?
Boot into Safe Mode, uninstall suspicious apps, and run a free antivirus scan. If needed, perform a factory reset after backing up your data.
How do I check if my phone is linked to another phone on Android?
Open your Google account and review the Devices section for unknown logins. Remove unfamiliar devices and enable two-factor authentication.
How-to Guides
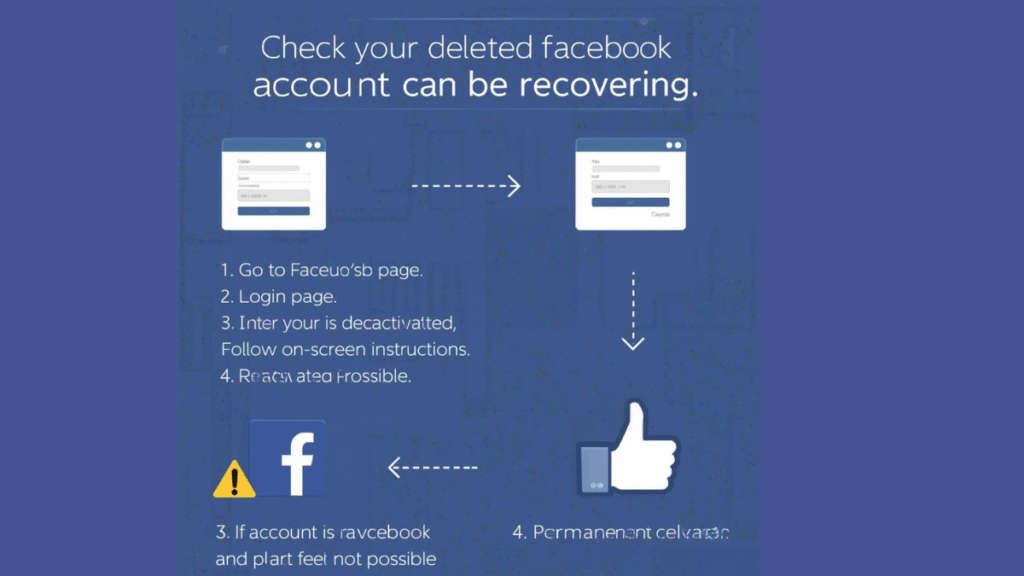
How to Know If You Can Get Back a Deleted Facebook Account (7 Clear Steps)
Losing access to a Facebook account can be confusing, especially when you don’t know whether it was deleted permanently or can still be recovered. Visit Facebook Help Center for (account deletion / recovery page) Many users panic after seeing login errors or missing profiles and start trying random recovery tricks that never work.
If you are searching for how to know if you can get back a deleted Facebook account, this guide explains the difference between deleted and disabled accounts, the exact recovery steps that work, and how to protect your account in the future without false promises.
Understanding the Difference: Deleted vs. Disabled Accounts
This is the most important step, and most people get it wrong.
Deleted Facebook Account
- Deleted by the user
- Can be recovered only within 30 days
- After 30 days, deletion becomes permanent
- Login and password recovery stop working
Disabled Facebook Account
- Disabled by Facebook due to policy or security issues
- Account still exists in Facebook’s system
- Can often be recovered through appeal and verification
Knowing this difference tells you whether recovery is possible or not.
Acting Quickly After Deletion
If you deleted your Facebook account yourself, time matters.
- Facebook gives a 30-day grace period
- Logging in during this time cancels deletion
- Waiting too long makes recovery impossible
If less than 30 days have passed, stop reading and try logging in immediately.
Using Facebook’s Official Recovery Tools
Always use Facebook’s official tools, not random websites.
Try these first:
- Facebook login page
- “Forgot Password” option
- Account recovery forms
If Facebook still recognizes your email or phone number, your account is not permanently deleted.
Recovering a Disabled Account
If your account was disabled instead of deleted:
- Facebook usually shows a “Your account has been disabled” message
- You may see an option to submit an appeal
Steps:
- Open Facebook’s appeal form
- Enter your registered email or phone number
- Follow on-screen instructions
Disabled accounts often have better recovery chances than deleted ones.
Checking Your Email
Your email inbox gives important clues.
Check for:
- Facebook security alerts
- Deletion confirmation emails
- Appeal or review messages
If Facebook recently emailed you about your account, it usually means the account still exists.
Using Trusted Contacts
If you set up Trusted Contacts earlier, they can help you recover access.
- Facebook sends recovery codes to trusted friends
- This works only if the account is still active or disabled
- It does not work for permanently deleted accounts
This option is often overlooked but useful.
Identity Verification
For disabled or locked accounts, Facebook may ask for identity proof.
What usually works:
- Government-issued ID
- Clear photo (not blurry)
- Correct name matching your profile
Recovery may take days or weeks, so patience is important.
Avoiding Third-Party Scams
Be careful many websites promise:
“Guaranteed Facebook recovery”
“Hack your account back”
“Pay to recover deleted ID”
These are scams.
Facebook never charges money for account recovery.
Using third-party tools can make things worse or lead to data theft.
Strengthening Your Account for the Future
If you recover your account or create a new one secure it properly:
- Enable two-factor authentication
- Save backup recovery codes
- Verify email and phone number
- Avoid suspicious links and fake copyright notices
Prevention is easier than recovery.
How Level Up PR Can Help
If your Facebook account is important for business, branding, or public presence, professional guidance can help you understand account risks, recovery options, and online reputation management.
please visit for more guide How to know if your Facebook account is hacked
Final Thoughts
You can get back a deleted Facebook account only if:
- Less than 30 days have passed
- Facebook still recognizes your login details
After permanent deletion, recovery is not possible.
If you want to know how to know if you can get back a deleted Facebook account, always check:
- Login access
- Password recovery
- Time passed since deletion
- Account status (deleted vs disabled)
Understanding these points saves time, stress, and false hope.
FAQ
How to know if you can get back a deleted Facebook account?
If login and password recovery still work and less than 30 days have passed, recovery is possible.
Can Facebook recover an account after 30 days?
No, permanently deleted accounts cannot be restored.
Is a disabled Facebook account recoverable?
Yes, disabled accounts can often be recovered through appeal and identity verification.
-

 Fashion6 months ago
Fashion6 months agoWhy ’90s Fashion Still Dominates Today’s Style Scene
-

 Fashion6 months ago
Fashion6 months agoTop Fashion Trends to Follow in August 2025
-

 How-to Guides6 months ago
How-to Guides6 months agoHow to Restore Pantone Colors in New Illustrator Versions (2026 Guide)
-

 Politics6 months ago
Politics6 months agoReddit Politics: A Deep Dive into Online Political Discourse
-

 How-To Tutorials & Troubleshooting6 months ago
How-To Tutorials & Troubleshooting6 months agoHow to Screenshot on Mac: The Complete 2025 Guide








